[Post 31 of 30]

In this recap post, I am going to lay things bare. Some thing worked well and some things fell flat. And I mean completely bombed. The goal of this post is to show the insights I gained from this experience, and hopefully others can get some benefit from walking through the process. If you want to go through the same process yourself, I don’t recommend it. It’s stressful and the risk of breaking the unwritten contract with your readership on the defined cadence, felt like a potential breach of trust.
Week 0. The prep week before:
The goal:
- Come up with 30 article topics, create high level outlines, and the flesh them out as time permits.
- Schedule posts a week in advance to allow for any issues that may pop up and compensate for it.
- Plan to do the bulk of the work on the weekend for the coming week
The outcome:
- I created the outlines of 10 posts
- I ended up scrapping most of them because I didn’t think they were good enough
- I had 3 in draft ready to begin posting before the start
- It took WAY longer than I anticipated. I ended up spending 4 hours per post, researching, compiling information, organizing my thoughts and determining how I wanted to convey the topic.
- I was slightly panicked because I wasn’t sure this was sustainable, but I was willing to give it a try regardless. – Whats a tainted reputation anyway?
Week 1. Lets get busy:
These are the stats for views (light blue) and visitors (dark blue)
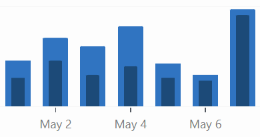
The first day, I did okay, then a bit better, with some ups and down. Day 5 and 6 were lousy, then day 7 was great!
What worked:
Topics on: MDR, AI, Zero Trust and Gamification
What didn’t work:
Topics on: SASE, cost optimization
Here are the posts for week 1:
Week 2. Analysis and commentary
These are the stats for views (light blue) and visitors (dark blue)
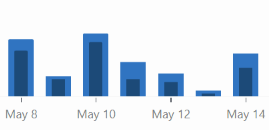
This week I decided to offer analysis and commentary. I reviewed an interview about the evolution of generative AI, reviewed an interpreted an annual cybersecurity report, talked about cybercrime law, and opined on hacker culture.
What worked:
Analysis on complex and evolving subjects that are normally exclusive because of jargon and pre-requisite knowledge.
What didn’t work:
Opinion pieces that do not have actionable information. Niche articles that only appeal to a very small segment. Unless you target that segment exclusively and grow your readership, expect a very small number of readers.
Here are the posts for week 2:
Week 3. Leveraging ChatGPT for Research and Perspective
These are the stats for views (light blue) and visitors (dark blue)
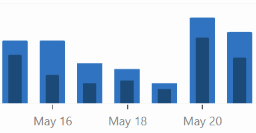
This week I started using ChatGPT (GPT4 model) to do research. This was a game changer for me. I was able to dive deep into a subject in seconds, bypassing the garbage I would normally wade through on the web. I could then take that content and re-interpret it in a number of ways to get a better understanding. Then build a narrative and make a post based on the end result. I could change my writing voice and perspective based on the who I was targeting. It felt like cheating, because I ended up with a great result, but I did put in a lot of work to get there. There was no “generate blog” button. It was a process, of research, analysis, framing, and introspection, but it ended up being so much more valuable, with less effort.
What worked:
Useful, tactical information that can be used immediately. There is so much information out there that people do not have time to go down rabbit holes that do not affect them directly.
What didn’t work:
Topics that were too high level and more of a thought piece, than something actionable. This is the same thing I found when I researched who actually reads whitepapers, or PhD dissertations. It is often only read by a very small handful of people, and only referenced (not read) by others. Think of that; YEARS of extremely hard work and research, only to have it shelved and get a suffix added to your name.
Here are the posts for week 3:
Week 4. Future Planning and Strategy. AKA; People like books!
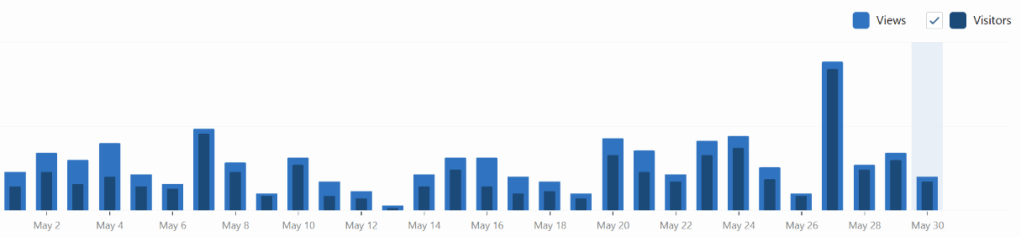
These are the stats for views (light blue) and visitors (dark blue)
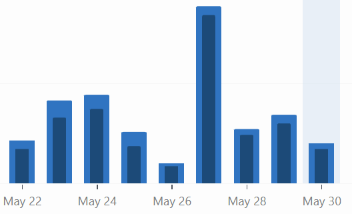
This week I focused on new things. Emerging threats, new threat actors, what CTOs and CISOs should look at and strategy planning. The results of this week blew me away. My post on cybersecurity books to read, blew away all other days by far. But my post on Volt Typhoon, which is a SERIOUS threat (that could accelerate global instability and be the catalyst for a new type of world war in the near future), got almost no reads.
What worked:
Clear actionable information. Seeing a trend here? Providing information that can save time and add value to things that people are doing already. Shedding light on new areas that are emerging and not a lot of detail is out in the public. My voice cloning post did very well in this regards.
What didn’t work:
Talking about existential threats. People don’t have time to worry about the big picture, when they can do nothing about it. They need to look at the here and now. Tactical information, not intangible. Talking about budget, finance, economics. I think this is due to target readership, they are not the best for that content. Hence, know your audience!
Here are the posts for week 4:
Conclusion:

For 3 days in the month, I published just after midnight, which skewed the metrics and made it appear as if 2 posts were done on the same day. This highlights the difficulty of doing this consistently.
For the last month, I have put a crazy amount of effort into coming up with content every single day that is relevant, insightful, provides value, and is interesting – both to me and to the cybersecurity community. This was very difficult to do with consistency and there were times that I struggled to maintain the cadence.
This has been a great learning experience, but I would not do it again, its very difficult and stressful. If this was a full time job, then maybe. However, I think that I can get similar numbers by providing deeper dives into topics, posted once or twice a week. The key is to know your audience and be committed to providing them value. I am not any sort of professional blogger, but I have learned a few things after writing over a hundred articles.
Lessons Learned:
- Have a consistent voice, strategy and target audience. Your audience gets to know that and becomes familiar with it.
- Know the target audience. Is it a single persona, or multiple? Craft your content for them, not for everyone.
- Add personality. Your voice is a reflection of character. People appreciate this. I sometimes struggle with this when providing very technical information.
- Provide enough detail, but not too much. Start with what you want to cover. End with a summary, or a call to action.
- Time your posts optimally. I found that the best time time for engagement for my content, was Wednesday at 9AM.
- Socialize across multiple mediums. LinkedIn account stream, LinkedIn Private groups, Twitter, Facebook, etc. Using something like Hootsuite
- Solicit comments in your posts, and respond to ALL of them. This creates engagement in the community.
What I also recommend, and will do more of in the future myself:
- Have focus themes. ie: This is identity week, or compliance week, or red teaming week, or podcast week.
- Use LinkedIn carousels for more engagement.
- Create content once and then cut it up into different digestible chunks for each social media platform, linking back to the original content, but being able to stand on its own as well.
- Build readership with subscriptions. Either by subscribing to the blog, podcast, or best, a newsletter.
- Engage more with people in the community. Comment on other content creators work. Don’t operate in a bubble.
- Build up your peers. Share, like and subscribe to others in your field, even competitors. We are all people, and technology is not a zero-sum game.
Discover more from Designing Risk in IT Infrastructure
Subscribe to get the latest posts sent to your email.