

Emanuel Figueroa
Emanuel Figueroa is a senior analyst for Security Market intelligence at IDC Latin America. He is based in Mexico and covers security markets in the Latin American region. As a security regional analyst, Figueroa oversees the Security Market for IDC Latin America and provides insights on cybersecurity trends, opportunities, and challenges in the region.
Figueroa’s expertise lies in analyzing the security market landscape, emerging trends, and vendor dynamics in the Latin American region for IDC’s clients and stakeholders
https://www.linkedin.com/in/emanuelfigueroa/
https://www.idc.com/getdoc.jsp?containerId=PRF005728

On todays episode:
Here are the key topics discussed:
- Multimodal Cyber Attacks: Emmanuel discusses the increasing prevalence of advanced threats such as deep fake video avatars and voice cloning used in virtual kidnappings and other malicious activities.
Responsibility for Cyber Protection: A deep dive into who is responsible for protecting individuals from cyber threats—government, law enforcement, companies, or individuals.
AI and Security: The conversation explores the impact of AI on cybersecurity, including the development of personal agents to filter communications and protect users.
Endpoint Security Solutions: Emmanuel explains how modern endpoint security solutions are evolving to address new threats like smishing and other phishing attacks.
Security Frameworks: The importance of security frameworks (CIS, NIST, ISO) and whether organizations should adopt a mixed approach to tackle AI risks.
Cloud vs. On-Prem Strategies: Insights into the ongoing debate between cloud-first strategies and the repatriation of workloads, especially with the rise of generative AI.
Hybrid Cloud Strategies: Emmanuel’s take on the necessity of hybrid cloud strategies and the steps organizations should take before adopting generative AI.
Below is the transcript of the podcast and some key points related to what was referenced.
[00:00:00] Daemon: So Emmanuel, we met over at a recent CDW BTEX conference in Toronto and it fantastic that I got a chance to meet you over there because I know you don’t come up over here for very often. And I think that was actually your first time up in, Canada. And the conference you were one of the keynote speakers over there.

[00:00:20] There was a lot of really interesting topics that were going on in terms of cybersecurity, some developments in the industry, and some of the things that they need to be concerned about ,.
[00:00:30] So, , I want to ask you a question that is related to some of these advancements , that are happening and specifically in regards to , artificial intelligence and some of the things that I’m starting to see in the wild. So, for instance, with artificial intelligence, there’s an advancement in the multimodal attacks that are happening on organizations right now.
[00:00:53] So you can have live deep fake video avatars, you can do voice cloning of [00:01:00] CEOs, And these types of things are used for virtual kidnappings, where you would actually have somebody that gets phoned up and then they have a clone, a child’s voice and saying, help, I’m being kidnapped and send money or something like that.
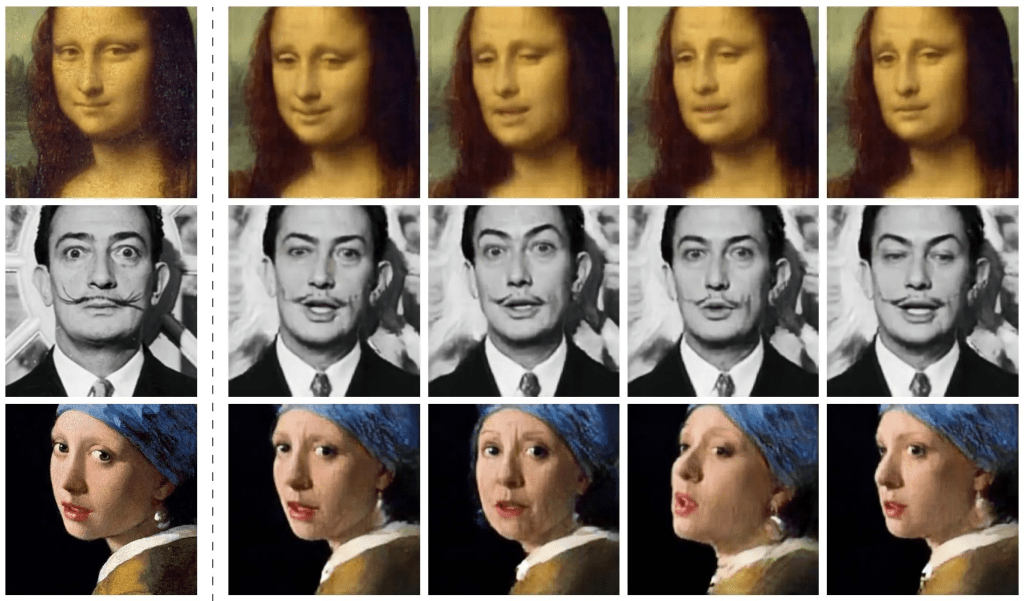
[00:01:17] Now, these are becoming more and more prevalent. But since they’re targeting individuals. Who do you think is actually responsible for protecting individuals and the general public? Would it be the government? Would it be law enforcement? Would it be the companies that are associated with , these people?
[00:01:35] Because ultimately, It may be companies that are being targeted through these sorts of attacks. So what’s your take on who do you think is responsible?
[00:01:46] Emanuel Figueroa: No, I really appreciate that question. And thanks for that. , it’s like, well, first of all I personally believe that every state on the world have the main responsibility to protect their individual.
[00:01:56] So as well as. As their human rights, for instance, [00:02:00] so, but on the professional side, maybe we have to understand that not all the countries have to comply with this, , and this in relation to the government, , on the other hand. When we see, , when we, we understand about law enforcement, is that, , law enforcement could be constrained by privacy sometimes, , so here’s when we have to think.
[00:02:19] About it. , it’s like maybe we have to find a new system in which we could serve, , or or law enforcement and government could serve as a sentinel just to protect their individuals based on their level of risk and responsibility. Right? Just like it happens in companies. So, and I don’t want to risk the importance today, academia, , because they, , you, , something important is prevention.
[00:02:40] So you have We have to regularly have some training in how to avoid the main risk in the use of technology, but I’m not always, , , I’m not all necessary, , like all the use of technology, but at least the technology that represents more. A risky scenario for companies like AI, , because we, , we are now [00:03:00] in this era, it’s more important.
[00:03:02] So, but if you ask to the C suites, because, , I had a chance to talk with a lot of people and what they are facing as their main challenges is that they face or, or try to prevent, , the face of in the face of implementation of Gen AI, for instance, they will tell you that the security remains.
[00:03:23] At first place, , when, when, when they are trying to implement this type of new technologies. So the reality comes that from defining new policies. So probably from the, , from the company’s perspective, they have to reinforce, , or trying to define new policies that must cover how their users are taking responsibility for that.
[00:03:44] Use of new technologies, like, , AI or AI type of technology. I would say, , it just depends. It’s like, I know that we hate this type of of answers because, , it’s like. Just depends. Yeah, I believe that the government has some level of responsibility.
[00:03:58] Then the law enforcement. [00:04:00] Also have some level of responsibility, but at the end, . Every single users have to be. , responsible or taking responsibility for, , the type or the use of technology and how to protect themselves. But also the companies have to provide some level of of training at least for, the users that, , not only their responsibility that they has in terms of how they are managing the data, but also, , how to protect themselves , , from this type , of, , So this is what I’ve, I’ve been thinking about.
[00:04:33] Daemon: Yeah. I think that this sort of a type of attack , is going to start helping build a new industry that will pop up and you can kind of see it with some of the consumer electronics that are, out in the wild right now, for instance, , with the Google pixel phones.
[00:04:49] If you have a call coming in and you don’t want to answer it, you actually get an agent that will pop up and start talking to the person automatically and saying that, , [00:05:00] say who you are, what your objective is, and then they’ll actually have the choice to respond to the call or not. I think that’s gonna become more and more common where Everybody will have their own personal agent that represents them to the general public.
[00:05:16] So when somebody is trying to call a person or get a hold of a person, they’ll need to go through that gatekeeper agent. in order to do that. So then you kind of have a scenario where you have agents talking to agents and then most of the communication that may happen on the internet, whether it’s through email or voice or so on may actually just be agents talking , to other agents, removing the, the, the personal side from that.

[00:05:43] So what’s, your take on that?
[00:05:47] Emanuel Figueroa: No, yeah, absolutely. I believe that. , I would say that, , it’s like Well, we have been seeing a lot of rationalization between type of technologies, trying to cover, trying to protect, , every single side of, of, of the [00:06:00] users, something that we have been seeing, that, , these MDM type of solutions, for instance, , they are not being following the same step as usual.
[00:06:08] And this is because I believe that, , , more of the security industry are concentrated totally , in enterprises, but I believe that there’s a sort of companies who, who are trying to consolidate all this protection into a single type of agent and trying, , to offer a single console for those type of purposes.
[00:06:26] And yeah, I’m trying to face every single situation from there, , but most for protecting, , executive type of communications, not necessarily for a common users. But yeah , I believe that the first step has been pushed by, , this bring your own device type of policies at the company.
[00:06:45] So I believe that these have been pushing a lot of interest and I believe that, , probably eventually . We can see , some protection specifically for mobiles that could, be totally integrated into, , an IT stack ecosystem. Not only , at level of, [00:07:00] of the age or data center type of infrastructure, but also, , for, for covering specific identities and, mobile type of use.
[00:07:06] Daemon: Any development on protection against smishing or anything like that where , you actually have texts going out over to people, like some ways that you could. have that go through a filtering mechanism where it can look at the context that may be associated with that and then determine whether or not it’s it’s a scam that sort of thing, whether it’s something that is malicious or dangerous, then flag that in some manner.
[00:07:34] Emanuel Figueroa: Yeah, yeah, absolutely. I believe that, , most of endpoint security type of solutions are trying to cover, , many of those aspects. I believe that In fact, I’ve been seeing that many of those solutions are trying to offering a risk scoring based type of solutions in which, , could give the sense , , to a company, for instance, through a single console, , the chance to see, , what is the level of risk that a [00:08:00] single, , user.
[00:08:01] Represents for the company in terms of avoiding this shadow it type , of data and consuming, right? But yeah, I believe that many of end point security solutions are trying to cover that, at least they are, , I believe that not necessarily the more common type of end point security solutions.
[00:08:18] They are more like mobile. Security solutions. And yeah, they are trying to cover this to encrypt, , giving the capability to encrypt the communications between one call to another, , trying to generate a single, , channel communication for protecting SMS and also for the for the calls.
[00:08:37] But I believe that this is more an executive mobile security platforms, but yeah, I’ve been seeing some sort , of those, but many of those are offered for for executive protection, not only, not necessarily, I’ve been seeing a massive grow for, for common users.

[00:08:57] Daemon: I think that for executives, it definitely makes a [00:09:00] lot of sense because they’re the high value targets, but , attackers can still come in and target other individuals within the company and then try to work their way in through pretexting and so on. So I think that over time, As the, the cost per user goes down, that it’ll become widely adopted through, various means.
[00:09:24] , I also think that at some point, There may be a way to profile the risk of different types of users based on their, their activities or how they use their, devices. So if let’s say for instance you have a company issued device and then, The user is doing activity, which may put them more at risk.
[00:09:47] Then that may flag them as a more risky individual within the, , company. So it’s not necessarily that they’re doing anything malicious or bad, but they’re putting themselves in situations that may be , more risky than others.
[00:09:59] Emanuel Figueroa: [00:10:00] Yeah, yeah, absolutely. And something I, maybe I can add something else and is that, , , , besides the fact that, , there are a specific type of solutions for protecting, , Those types of behaviors, , we are also seeing that, , , the growth , in software as a service type of adoptions, , , and from that standpoint, I would say, , a good number of vendors are trying to offer, , protection to a many collaboration type of solutions, like, , this CASBE or CDLP or, , like, or DLP specifically , for those type of users, just for avoiding, , this shadow it type of behaviors.
[00:10:33] And yeah, but. I believe that this cloud security posture management type of solutions also trying to cover, , many of those aspects, even when we are really seeing, , this gap in between, , enterprise types of solutions and also, , this more user behavior or, , this solution driving specifically for users, right?
[00:10:53] Daemon: Yeah, and that kind of leads into my next question, which is in regards to the, the approach of the [00:11:00] strategy that our organizations take to implement security frameworks in, in their environment. So whether an organization has decided to go down the path of CIS or NIST or ISO and, , use whatever framework fits their organization.
[00:11:19] As they start moving over to leveraging artificial intelligence and looking at the risks that are associated with that and they’re emerging all over the place. And it’s, it’s a very new. Set of technologies , that are really being leveraged in different ways than they have before where artificial intelligence , of the, the past or, , what was called GOF AI or, or good old fashioned AI.
[00:11:45] It was very isolated and it was, it was back office stuff. It didn’t really interact with the rest of , the enterprise, but as organizations are moving towards. To adopt generative AI and have it connected to every aspect of their environment. And , [00:12:00] do coding, interact with clients, everything that you can imagine.
[00:12:04] There’s new frameworks that are popping up to implement certain security controls around that. And like, there’s the the NIST AI risk management framework. There’s ISO 42001. So if an organization has already adopted a security framework, does it make sense for them to continue along that same path?
[00:12:25] And like if they have iso, should they continue on with ISO 42001 for AI risk? Or does it make sense to have a mixed. Framework where you may have different types of frameworks overlaying in on top of each other in the enterprise.
[00:12:43] Emanuel Figueroa: No, yeah, . I believe that. .
[00:12:45] , I can tell you that the main approach always comes along with the with the business. And I mean, usually we took like, ISO 2xxxx because. , this is the door of entrance to establish new businesses with other companies, , third [00:13:00] parties.
[00:13:00] But once you comply, or you already notice that, yeah, maybe I’m in the level of maturity that I need to to to be your, , you, you understand that not necessarily you are or your stack. It’s infallible, , and so you have to start thinking in how to how can I. Set some compensatory controls that can really help me to protect my assets because now I comply with a, with a sort of framework, but not necessarily, , it’s like, , you comply, but not necessarily being are safe.
[00:13:29] Right. So here’s when do you kind of start thinking in using, , this type of frameworks like needs, because needs is going to give you, , or depending in where you are in this. Beautiful circle of evolution, , You had a chance to understand, , how to set new other frameworks, depending on your needs and that, that could cover, , specific type of needs, like AI, for instance, I’m going to, to start using AI type of infrastructure.
[00:13:56] So maybe I need to, to understand how to put controls [00:14:00] to protect the AI infrastructure, even when, when maybe I have to develop a specific policy for, , for my users to, How to consume AI that, but really is the second way of thinking this, this type of things. So I believe that, I believe that this is a process in which you have to tailor your specific type of framework.
[00:14:18] So you have to pick the most interesting controls from every single framework, and maybe you have to build your own Frankenstein because this is the way that we do, , in practice, , this type of things, , you have to pick the most relevant controls and create your own, Thing because, , the, the only, , the, the, the one who probably are more or that could understand in a better way how to address every single need is, , your, your own company.
[00:14:43] So you have probably to, in the process, you have to face a lot of colleagues just for understanding if, if that control it’s, it’s going to be able to, to, but for saying something like. It’s, it’s be able, , it’s something that we can do because [00:15:00] it’s not only about setting controls.
[00:15:01] It’s setting controls, but also understanding that this could be possible, , it’s like that this could be. Reliable and could give really not necessarily a good sense of, of, of being secure, but also that could be functional that could communicate with the business in terms of, , how we are going to control the data, how to be at a very good Level of risk management are also, , understanding that this could be possible without affecting any part of the business.
[00:15:34] Right? So this is so, but at the end, what we can say, or I can say about this is that, yeah, I believe that mixing frameworks is still is. It’s a way of doing this. And yeah, I believe that sometimes maybe, or maybe you can need some help in how to better approach to a very good set of, of these type of frameworks.
[00:15:55] And maybe the, so if you don’t know, , it’s like any of us understand [00:16:00] every single framework, right? Like probably you can understand a couple, but maybe you can ask some colleagues or some other people. Type of services for trying to understand how to better address these needs and how to gain all the , all the power of these frameworks to have a better risk.
[00:16:17] , posture and also, , to understand how can I, , advantage of those type of. Of those of solutions, or maybe, , trying to. , to, to code, , this long path in order to get the level of maturity I wanted through this type of services. So this is, this is my approach, but this , it’s like you are going to adopt any other framework, depending on where you are in, in, in that curve of, , , evolution or immaturity evolution.
[00:16:48] Daemon: Also in terms of mixing different frameworks and the fact that many organizations now are dealing with other entities and supply [00:17:00] chain that are global. Ensuring that the global partners adhere to a certain set of security standards , is important and becoming more and more. So so who do you think gets to dictate what standards get used in the supply chain process?
[00:17:21] Like if you have an organization that is. Defined as a supplier, they’re adhering to local standards and some international standards as well. Then they, they have a customer that has another set of standards, but doesn’t necessarily adhere to the same ones. How do they overcome the gap in between those different standards?
[00:17:46] Emanuel Figueroa: I believe that’s a good one. Well, first of all,, what Usually prevails. The international standard. So first of all, you have to take the international standard and try to cover, , every single need interest of your own company. And then [00:18:00] probably you have to take a look , into the local standards and trying to cover, , as much as possible.
[00:18:06] But at the end, when you have to start new businesses with other companies, you have to start making some type of mapping, like how my local framework or my local, , Standards, , are going to communicate with my third party , for instance, I recall in my previous experience, , I recall, I’ve was conducting a third party security reviews in which, , we have , this local standard , that has some level of inheritance from, from the international standard.
[00:18:34] And , we have to map, , how. We are covering every single point from the requirement of the of our customer or our third party partner and yeah, , if there is something that it’s outside our standard, maybe we have to, , add some. Other definitions, but I believe that this is the usual way.
[00:18:54] This is a way that already works and . I recall a very good project in [00:19:00] which I’ve been part. And yeah, they decide for instance for privacy and I don’t know this is not necessarily the main topic but just for sharing a good example is that , we all understand that GDPR it’s a pretty good standpoint for privacy, right?
[00:19:15] So, , this this customer decides to take GDPR And all the, , all the local standards from every single country in the world, and they elaborate a single standard that covers every single of the hard standards just to cover privacy as , and to have a very good understanding and a consolidating and sharp and, concise type of, framework for covering every aspect of the business I believe that this, function very well. So what also I can say is that, yeah, even, even a framework or policy or a standard have to be flexible, right? So the more flexible you are, the more easy will be , , to [00:20:00] accomplish your goals in this area.
[00:20:01] Daemon: . The last question that I have for you is. In the past few years, there’s been a big push to go to the cloud. It was a cloud first strategy. Everything’s going to the cloud. Then after that, organization started looking at The costs that are associated with that, that the skill that’s associated with that, the fact that it’s actually very difficult in order to move applications to, the cloud, unless you actually do refactoring, some things can’t be refactored.
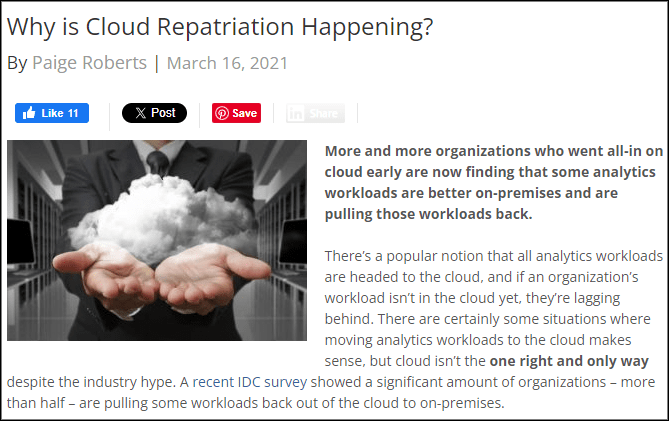
[00:20:30] So, if you do a lift and shift, put in the cloud, then it doesn’t make financial sense in order to do that because it’s. , just putting it in a different data center and you’re paying more for the exact same service. So what some organizations have been doing is doing a bit of repatriation of these workloads that went to the cloud, bring them back into , the data center and and then reanalyze the costs that are associated with that and the security that’s associated with that.
[00:20:56] But on the other side of the spectrum, [00:21:00] we have AI that comes into the picture. And generative AI specifically, where if you want to make use of the best models that are out there, the, largest ones, the GPT fours, the Gemini is all that kind of stuff that’s all running in the cloud. So you have to start building the environment to leverage that, that cloud.
[00:21:20] So , it’s kind of an opposite. Of a trend that’s happening in the industry. And , what’s , your take on that? Should organizations have a dual strategy from that perspective, or should they start moving some things over to the cloud and then some things back on, on prem? How do they.
[00:21:40] repatriate things and then move things into the cloud at the same time while maintaining security , and governance for their entire environment.
[00:21:50] Emanuel Figueroa: . Yeah. I believe that. And thanks for that. , it’s like something that, that I’ve been seeing is that repatriation. It’s more a matter of understanding [00:22:00] how the things are going to work in, in cloud, , it’s like, , , even now it’s, at least for me, it’s stunning to see how many organization , are still understanding this share responsibility model?
[00:22:13] Between an hyperscaler and their own company on how they are going to consume the data. This micro segmentation type of technology is something that they are not necessarily familiar, , even when they have already a lot of experience about how to, , create new applications and how, to use Kubernetes or this type of, Solutions.
[00:22:32] So I believe they were trying to use the technology as they were accustomed to, , like, , premise, right? , you cannot imagine right now, for instance, to have , ACM on premises and have all of your resources in cloud trying to , sending data out of the cloud, right?
[00:22:48] Because it’s going to to rise your expenditure ,, but , once they understand the capabilities of cloud and how they can leverage from those, , I would say , Those type of micro segmentations and, , like [00:23:00] micro services type of solutions, they understand that there is a level of complexity that they have to face.
[00:23:06] And they have to start by understanding this new paradigm shift between cloud and on premise. And then , now that they are starting to implementing these AI type of projects, they understanding that cloud would be, , their most proliferate and, , their most friendly , ally in terms of how to adopt technology.
[00:23:28] So they understand that they have to comply. Also with the use of AI as any other type of technology. So the more , a company understand this, how to consume the cloud and how, it work and how to communicate between all their ecosystem.
[00:23:46] They are starting to understanding that, , cloud strategy is part of their, new initiatives, right? Like AI for instance, and I believe one of the most. The most interesting topics about AI has to be related to [00:24:00] how all this type of gen AI type of technologies are going to cover also on prem type of solutions and also, , cloud type of solutions, and the more they are open like an open model , they are going to have more relevance , to their own security.
[00:24:18] I believe that there’s a lot of misunderstanding from customers in terms of how they are acquiring , new technology like AI. But also How they are consuming , the data and where the data , has its residency, right?
[00:24:33] So it should depend on the situation, but I believe that most of them are going to Accelerate their consuming in cloud because You cannot think that your business is going to grow without the use of cloud, ? So when you have a very Huge project using a specifically AI for growing your business.
[00:24:50] You’re going to need, , to have a cloud strategy. And I’ve been seeing that, , most of the first, early adopters are trying to cover both aspects , [00:25:00] of their,, evolution, it’s like, , you’re going to think. Having just on prem type of solutions, you have to think that cloud is going to give you , the speed , , flexibility, , elasticity that you will need for growing your business at a time that it’s needed.
[00:25:14] , despite the fact that you are adopting or not AI, this is one of my approaches.
[00:25:20] Daemon: , I think that most organizations, regardless of the size or what they actually do, will need to have a hybrid cloud or multi hybrid cloud strategy. And then leverage the resources as they, need them, whether it’s infrastructure as a service SaaS, or functions as a service.
[00:25:38] And then determine what makes the most sense. But for organizations that have a traditional legacy infrastructure on prem, and they want to leverage some of these new generative AI capabilities in the cloud, What do you think they should do before , they do that? Should they implement an AI security [00:26:00] policy?
[00:26:00] Should they have a cloud security policy? Should they approach things from another holistic manner? What steps should they take before they start adopting generative AI? You
[00:26:12] Thanks for that. Personally, I think that they have to understand the use case of gen AI because , it’s like, a couple of weeks ago, I being in RSA in San Francisco.
[00:26:22] Emanuel Figueroa: And I recall that, , we have a lot of conferences with regards AI and how this is going to, , resolve a lot of issues. But I believe that the thing that many companies have to take in count is, , what is the issue? What is the main. Issue that it’s going to resolve, , If Gen AI is not necessarily going to resolve a specific use case, maybe we have to rethink, , if it’s time to start with some kind of project like that.
[00:26:49] So, I believe that we like to say that in Gen AI, there are 2 different type of use cases, , the, the 1 related to automate the mundane task of the analyst and the other [00:27:00] type of use cases that is related more to, , up leveling. The security professional capability. So they have to understand what is the part of the business that this gen AI is going to resolve and what are the security outcomes that they are going to obtain from this type of projects.
[00:27:15] And then, yeah, absolutely. I believe that this is going to provide a lot of optimization and automation into the company. And, , not only , , to create a new role as a prom engineer and just, , sending messages through this type of tools. I believe that have to be related to, a business goal.
[00:27:35] , , I don’t mean to be simplistic, right? But, , if companies start to adopt a technology. That they are not necessarily understanding what is going to solve, , it’s like to buy a car for your garage. So you are not going to exploit, , all the capabilities from from that type of solutions.
[00:27:53] So this is something important. And then, yeah, understanding, , what is going on. How this is going to converse and, , because [00:28:00] it’s about data, , and you need to understand that, , the level of data that you are going to need for generating all the value depends totally in what is your level of preparation.
[00:28:11] Right? So if you are not. At a standpoint in which you can exploit, , a very huge amount of data, probably you, need to start by, , creating a data lake or, , a huge repository of data that could going to this type of, of, of solutions. So this is something I’ve been thinking, and I believe that, yeah, in gen AI , , all it’s about data, right?
[00:28:34] So this is something interesting.
[00:28:37] Daemon: Yeah and I was reading about that recently, that when organizations start going through the process , of implementing generative AI and retrieval augmented generation, which basically points to internal documents that they may have in their environment, , the biggest risk is actually things that maybe latent vulnerabilities or risks [00:29:00] or exposures that they have in their environment that are actually brought to light through this process.
[00:29:04] So, things such as poor permissioning of the environment things that are exposed that are, aren’t supposed to be exposed that sort , of thing. So, as organizations start going through this process of incorporating internal data into generate AI, I think it’s a good opportunity to do a full review of their entire environment to see where there are gaps in their security posture, in their strategy, before they start exposing those to a greater risk that that they could , through generative AI.
[00:29:38] Emanuel Figueroa: Yeah, absolutely. I’m totally agree with that. , it’s like, for instance, when, a CISO practice when you come to a new company, right? Like you have first to assess, , your security posture, , before I started working in, what are the things that you have to improve?
[00:29:52] And, , what are the things that probably you have to take over on? So, yeah, absolutely agree.
[00:29:58] Daemon: Yeah, so thank [00:30:00] you very much for coming on the podcast. Really appreciate it. Fantastic conversation that we’ve had so far. Before we sign off on this episode do you have any final thoughts that that you would want to provide to, to our listeners?
[00:30:15] Emanuel Figueroa: First of all, , , I always. Try to, share with a lot of companies that , , technology. , absolutely. It’s going to help us in resolving all the issues, but we have to understand the benefits that the solution is going to give us and the benefits. But by the benefits, I understand, , how the solution is going to, cover .
[00:30:36] My concerns are my challenges in the company. Now, this is going to converse with that, , but also we have to understand that, , despite the fact of these gen AI type of solutions and , we understand that in the market, , like AI and ML has, , a lot of years before that has been, , putting in practice with a lot , of vendors.
[00:30:54] So we have to be totally. Clear in how those type of solutions are going to [00:31:00] resolve our own needs and what are the security outcomes that are going to generate for us to, to achieve our business requirements, , , and also something , that could be interesting.
[00:31:11] It’s yeah, we have. To have clear that, , every single solution needs to help us to show , the board of directors and, , , all these, , bigger tables, , , how to achieve a better risk perspective. It’s not all about. The data, , if, if risk is not measure, if risk is not pretty clear from our standpoint, probably we were going to have some issues in how to gain the backup from, from the board of directors.
[00:31:41] , we have to see the benefit. We have to see how this type of solution that are going to scale with my business, but also, , how it’s going to generate. The security outcomes we are expecting from them. This is something , I like to share with your audience and .
[00:31:55] Thank you very much for having me here. , it’s an amazing conversation and hopefully in the [00:32:00] future we can have another one.
[00:32:02] Daemon: Do you have, any contact information that you would like to share with anybody would want to get in touch with you or websites or anything like that?
[00:32:10] Emanuel Figueroa: No, yeah, you can find me as Emmanuel Figueroa through LinkedIn, . Yeah, if you want to take a look into, , the reports that we have preparing, , you can, find me as Emmanuel Figueroa at IDC.
[00:32:21] com. So, please feel free to take a look.
[00:32:25] Daemon: Great. Thank you very much.
[00:32:28] Emanuel Figueroa: Thank you.
Further Research on the topics covered.
- Multimodal attacks like deepfake videos and voice cloning are becoming more prevalent for virtual kidnappings and targeting individuals. [https://www.csoonline.com/article/3645116/what-is-a-deepfake-and-how-are-they-created.html]
- Governments have the main responsibility to protect individuals, but not all countries comply with this.[https://www.un.org/en/about-us/universal-declaration-of-human-rights]
- Law enforcement can be constrained by privacy concerns when protecting individuals.[https://www.eff.org/issues/law-enforcement-access]
- Companies should provide training to users on risks of new technologies like AI to prevent attacks.[https://www.sans.org/cybersecurity-resources/cybersecurity-awareness-training]
- Personal AI agents could act as gatekeepers to filter communications and protect individuals.[https://www.forbes.com/sites/bernardmarr/2022/03/25/the-amazing-ways-how-ai-virtual-agents-will-transform-our-world/]
- Mobile security solutions are emerging to encrypt communications and protect against smishing attacks.[https://www.csoonline.com/article/3645116/what-is-a-deepfake-and-how-are-they-created.html]
- Risk scoring based on user behavior can identify risky individuals within a company.[https://www.gartner.com/en/information-technology/glossary/user-entity-behavior-analytics-ueba]
- Cloud security solutions like CASB and DLP aim to prevent shadow IT behaviors.[https://www.cisco.com/c/en/us/products/security/cloud-access-security-broker.html]
- Established security frameworks like NIST and ISO have new extensions for AI risk management.[https://www.nist.gov/itl/ai-risk-management-framework]
- Companies may need to mix multiple frameworks to address their specific security needs.[https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2022/combining-security-frameworks]
About the author

With 25 years of industry experience, Daemon Behr is a seasoned expert, having served global financial institutions, large enterprises, and government bodies. As an educator at BCIT and UBC, speaker at various notable events, and author of multiple books on infrastructure design and security, Behr has widely shared his expertise. He maintains a dedicated website on these subjects, hosts the Canadian Cybersecurity Podcast, and founded the non-profit Canadian Cyber Auxiliary, providing pro bono security services to small businesses and the public sector. His career encapsulates significant contributions to the IT and Cybersecurity community.
Other recent articles of note.
Discover more from Designing Risk in IT Infrastructure
Subscribe to get the latest posts sent to your email.