
What is the Verizon DBIR?
The Verizon Data Breach Investigations Report (DBIR) is an annual report that analyzes and presents data on cybersecurity incidents and data breaches. It is widely respected and closely followed in the cybersecurity industry due to its comprehensive and data-driven approach.
The DBIR leverages data contributed by dozens of global organizations including law enforcement agencies, cybersecurity companies, and other organizations involved in cybersecurity incident response. It covers a wide variety of incidents from simple cases of stolen laptops containing sensitive information, to complex cybersecurity attacks on large corporations. The report typically includes analysis of tens of thousands of incidents and confirmed data breaches.
Key findings of the 2023 report:
Based on the 2023 Verizon Data Breach Investigations Report (DBIR), here are some of the top findings, their relevance, and suggestions for risk mitigation:
1. Social Engineering Attacks:
These attacks, which often take the form of Business Email Compromise (BEC) attacks, have almost doubled and now represent more than 50% of incidents within the Social Engineering pattern.
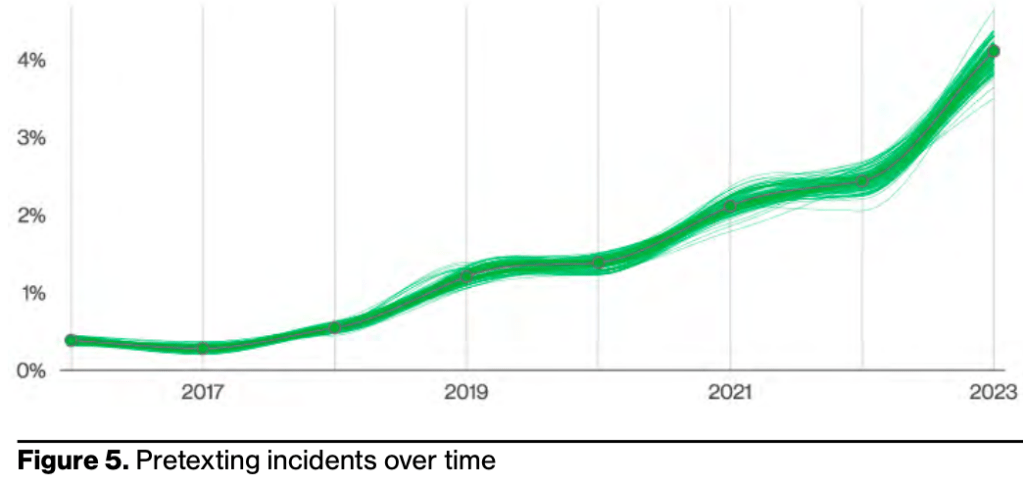
Social Engineering attacks are often very effective and extremely lucrative for cybercriminals. Perhaps this is why Business Email Compromise (BEC) attacks (which are in essence pretexting attacks) have almost doubled across our entire incident dataset, as can be seen in Figure 5, and now represent more than 50% of incidents within the Social Engineering pattern.
– Verizon 2023 DBIR
Relevance: Social engineering attacks exploit the human factor, which is often the weakest link in security. They are very effective and extremely lucrative for cybercriminals.
Risk Mitigation: Organizations can conduct regular security awareness training to help employees recognize and respond appropriately to social engineering attacks. This can include exercises in identifying phishing emails and other deceptive tactics.
2. Human Element in Breaches:
The human element is involved in 74% of all breaches, with people being involved either via Error, Privilege Misuse, Use of stolen credentials or Social Engineering.
74% of all breaches include the human element, with people being involved either via Error, Privilege Misuse, Use of stolen credentials or Social Engineering.
– Verizon 2023 DBIR
Relevance: This underlines the role that human error and behavior play in cybersecurity incidents.
Risk Mitigation: Organizations should focus on creating a security-conscious culture, providing regular training on cybersecurity protocols, and implement strong access controls and privilege management systems.
3. Ransomware Attacks:
Ransomware remains one of the top cyberattack methods, accounting for 24% of all breaches, and is ubiquitous among organizations of all sizes and industries.
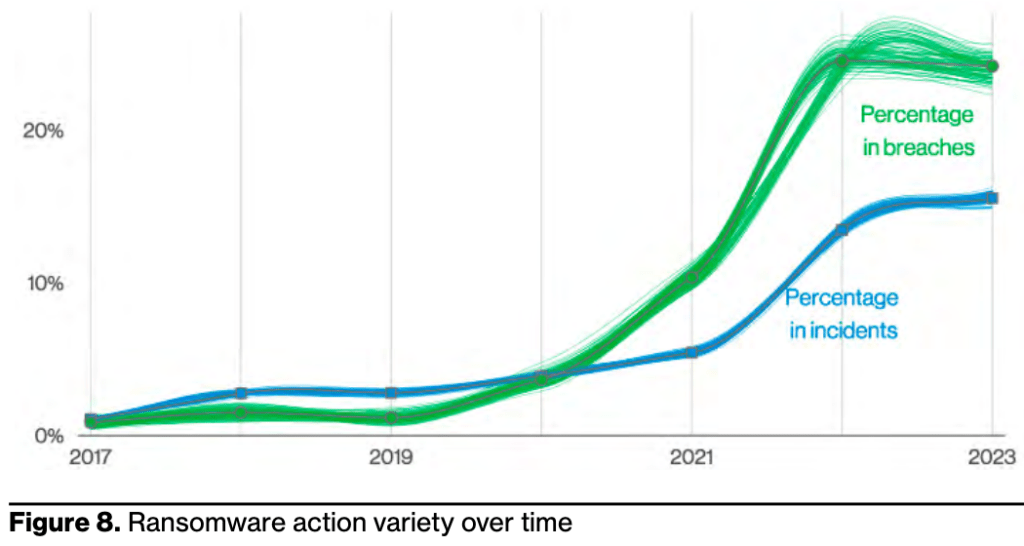
Ransomware continues its reign as one of the top Action types present in breaches, and while it did not actually grow, it did hold statistically steady at 24%. Ransomware is ubiquitous among organizations of all sizes and in all industries.
– Verizon 2023 DBIR
Relevance: The continued prevalence of ransomware indicates that it remains an effective strategy for attackers, impacting both small and large organizations.
Risk Mitigation: To mitigate the risk of ransomware, organizations should maintain up-to-date backups, keep their systems and software updated, use reliable security solutions, and conduct regular cybersecurity awareness training that includes the risk of ransomware. The ability to identify and respond quickly to a breach vastly reduces the chance of a ransomware attack occurring.
4. Log4j Vulnerability:
More than 32% of all Log4j scanning activity occurred within the first 30 days of its release, with 90% of incidents involving an exploit vulnerability having “Log4j” or “CVE-2021-44228” in the comments.
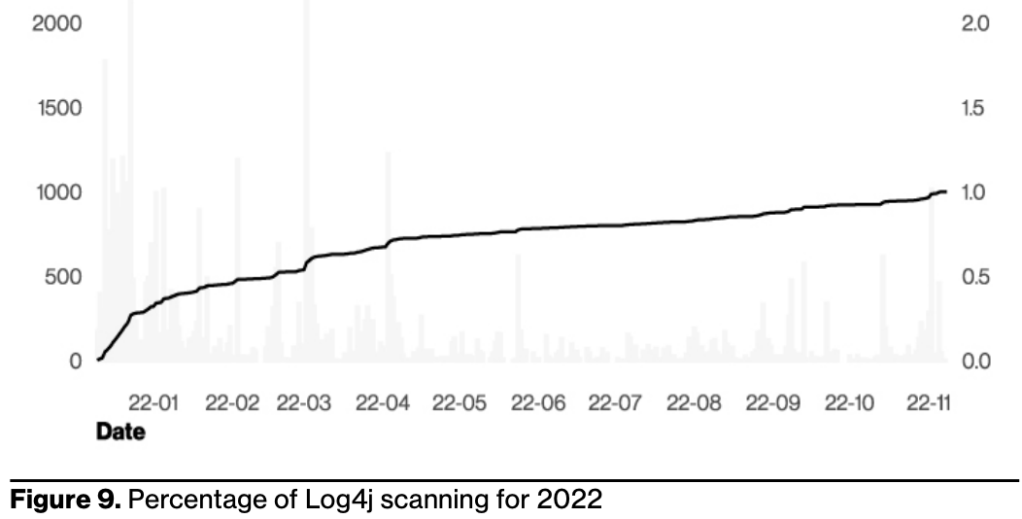
More than 32% of all Log4j scanning activity over the course of the year happened within 30 days of its release (with the biggest spike of activity occurring within 17 days).
– Verizon 2023 DBIR
Relevance: This emphasizes the speed at which attackers can exploit new vulnerabilities, especially high-profile ones like Log4j.
Risk Mitigation: Organizations should have a strong vulnerability and patch management process in place to ensure that they can quickly respond when new vulnerabilities are disclosed. They should also have an incident response plan for managing breaches when they do occur.
5. Senior Leadership as a Cybersecurity Threat:
Senior leadership poses a growing cybersecurity risk as they possess the organization’s most sensitive information and are often among the least protected. Executives and board members have on average 18 different threat actor groups targeting them directly at any given time.
Relevance: Senior leadership’s access to sensitive data, combined with often lax security protocols, makes them attractive targets for attackers.
Risk Mitigation: Organizations should ensure that security protocols apply equally across the organization, including senior leadership. This may require additional training or awareness initiatives targeted specifically at these individuals.
Summary:
To protect against the specific trends that have been identified, it is important to put more focus on the mitigating controls that combat them. I highly recommend reviewing the actual report, as it dives deep into the CIS controls you should focus on for this.
A simplified view of it is the following:
- Create a culture of security, not just policies. Things like security awareness, gamification of internal micro-learning, the capability for users to report phishing, BEC, or other suspicious activity, and ingraining that security is a team sport
- Have full visibility across your environment. The only way to know what is going on, is to have an inventory of all assets and services. Then implement continuous vulnerability scanning.
- Have a scheduled patching strategy. But be able to deviate from that and respond more quickly if a threat from a new vulnerability like Log4J warrants it.
- Have the capability to respond to incidents quickly. This can be done by developing internal processes, people, and systems to gather threat intel, review logs in real-time and have 24/7 coverage. Or it can be done by leveraging 3rd party services like MDR / XDR (Managed Detection and Response / Extended Detection and Response).
- Have an incident response plan. This includes involving all stakeholders into the conversation, not just IT, but management, executive, etc. Plan for the worst case scenario, so the worst won’t happen. Use Crisis Exercises and Tabletop Exercises to have deep and open dialogue. Get an Incident Response Retainer so you can get a dedicated team in there if stuff hits the fan. Get Cyber Insurance to transfer the remaining risk that you have not mitigated. If you can’t qualify for it, then at least follow all the recommended security controls.
Author:

Daemon Behr is a seasoned industry professional with over 25 years of expertise in IT Architecture, Systems Engineering, and Security. He has authored and made significant contributions to numerous books in the field. Additionally, he serves as the content creator and maintainer of this website. Daemon is the host of the renowned Canadian Cybersecurity Podcast and has been invited to speak at numerous IT conferences across Canada and the United States.
Discover more from Designing Risk in IT Infrastructure
Subscribe to get the latest posts sent to your email.